The typical organization
has invested heavily in solutions protecting against threats from
inbound e-mail such as malware (viruses, worms, Trojans, and phishing,
for example) and spam. However, the compliance and intellectual
property risks of internal and outgoing e-mail have not generally been
given much consideration. The retention policy and managed folder
technologies that provide messaging records management in Exchange
Server 2010 can aid in dealing with these issues for e-mail residing in
mailboxes (at rest), but they depend to a large extent on decisions
made on the content of messages by end users and, in some cases,
administrators. These decisions typically focus on the designation of
messages based on their content, principally in the context of their
intended use, audience, retention, and so on.
E-mail classification adds visual
labels and metadata to e-mail messages to describe the intended use of
or audience for a message to enable processes to make decisions based
on those designations. The message sender typically applies the message
classifications, as a decision made on the content of the message
before it is sent. These classifications typically indicate the
sensitivity, intended distribution, retention periods, or other
designations, usually as required by the organization. If deployed with
some pre-planning, message
classifications can offer a crucial piece of an effective strategy for
managing and controlling e-mail by ensuring regulatory compliance and
maintaining policy.
Unclassified, Confidential, and Secret are some examples of message
classifications used by organizations, whereas others may employ
designations such as Non-Business, Partner Confidential, Mergers and
Acquisitions, Privacy Act, and so on.
As with retention tags, AD RMS templates, and managed folders, the number of message
classifications should be kept to a minimum. This aids in keeping the
interface uncluttered for end users, which will in turn encourage them
to actually use this new technology.
In Outlook 2007, Outlook 2010, and Outlook Web App in Exchange Server 2010, the message
classification applied can display visual labels for the sender and the
recipients of the e-mail in the form of a user-friendly description of
the classification.
Note:
Message
classifications in Exchange Server 2010 are informational only; they
are not integrated with any transport rules or messaging records
management functionality. However, they can be used as a predicate in
transport rules, and transport rules can be configured to apply a
message classification as an action.
In addition, Exchange Server 2010 message
classifications set on a message are only visible to the recipient when
viewed in Outlook Web App, or with Outlook 2007 or Outlook 2010;
Outlook 2007 and Outlook 2010 require additional configuration to apply
and view Exchange Server 2010 message classifications.
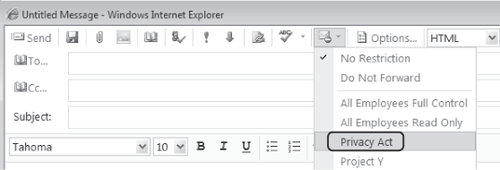
When a user composes a message in Outlook Web App and Outlook 2007 and higher, the message
classifications configured in Exchange Server 2010 are listed in the
Permissions dialog box, along with AD RMS templates, as shown in Figure 8-28. In this example, Privacy Act is a message classification, whereas the rest of the entries in the list are AD RMS templates.
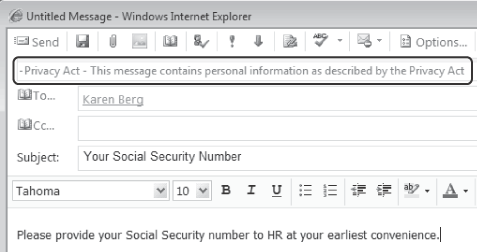
Message classifications are created using the EMS and the New-MessageClassification cmdlet. It is worth noting that the message classification selection seen in Figure 8-28 is just the display name of the classification. You specify the classification's display name with the DisplayName parameter; this defines the label seen from the selection menu by the sender. The SenderDescription parameter defines the description that is shown to the sender in the composed message, as shown in Figure 8-29.
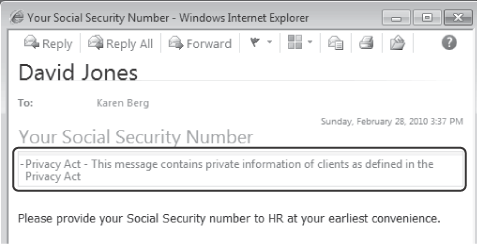
You can configure separately the text displayed to recipients of a classified message with the RecipientDescription parameter; the recipient description for the message composed in Figure 8-29 as seen in Outlook Web App is shown in Figure 8-30. If the recipient description is not configured, the text configured for the sender description is displayed.
|
Ed Banti
Program Manager, Microsoft Corporation, Redmond, WA
All too often
organizations will attempt to place rigid or complex policies on their
end users in the name of governance, compliance, security, privacy, or
a whole collection of laws and regulations. For example, I've heard of
organizations that prompt their employees to classify every single
e-mail and that process involves understanding the definition of
hundreds of classification tags and picking the right one. I've also
heard of organizations that give their employees complex instructions
on when to IRM-protect documents or when it's appropriate to S/MIME
encrypt versus sign an e-mail. While the intent is to keep the
organization and employees out of trouble, this approach results in
employee frustration and ultimately leads to the "click the default"
and ignore mentality, which is contrary to the original goal and intent
of the policy.
Instead of pushing complex
rules to employees, organizations need to consider ways to reduce
confusion and streamline the process. An easy way to do this out of the
box in Exchange 2010 is via message classifications and transport rules. Message
classifications are informational policies that can be tagged (either
manually or automatically) to e-mail messages that can display a
user-friendly description in Outlook or OWA. These message
classifications can then trigger transport rules in the background.
Take a look at the following example.
Contoso is a healthcare
provider with patient information that needs to be kept confidential.
Today they instruct their employees to include a disclaimer on all
e-mails that contain patient data and they also require that these
e-mails be encrypted. Half the time, employees forget to do this or
they only include the disclaimer but don't encrypt the mail. To
simplify, Contoso creates a set of message classifications: Patient
Data, Financial Data, and Public. When an employee marks and sends a
message as Patient Data, a transport rule is triggered that
automatically adds the proper disclaimer to the message and protects
the message using AD RMS such that the content cannot be viewable
outside of Contoso. For Financial Data e-mail, a transport rule applies
a different disclaimer and forces the message to be moderated before
the message can leave Contoso. This ensures that no financial data is
sent outside the company without approval.
As this example shows, you
have access to simple and straightforward ways to use message
classifications to abstract complex policies and actions from employees
while encouraging them to properly handle and classify sensitive
information.
|